How can we help you?
Connect DMC to Azure AD via OIDC
You can create an OpenID Connection, or OIDC, with Azure AD to DMC. This allows you to use SSO to authenticate and authorize individuals to use DMC. Follow the steps below to setup this connection.
Note: It is important to note that Azure AD does not support LDAPprotocol or Secure LDAP directly. It is possible to enable Azure AD DS instance on an Azure AD tenant with correctly configured network security groups. Learn more here
Instructions
Tip: Before you begin, you need an Azure account with privileges that allow you to manipulate app registrations, groups, and permissions. Then you need an app registration in Azure Active Directory.
Keycloak Steps:
- Go to the Keycloak admin console and find the Identity providers menu.
- Add an OpenID Connect v1.0 provider.
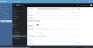
Azure AD and Keycloak Configuration Steps
This section covers how to setup an identity provider which provides the connection between Azure AD and OIDC.
- Type in the desired Display name.
Note: This is a visible name for your custom identity provider. In the provided example, we use OpenID Connect Login as the Display name.
- Obtain the client secret by generating one in the Certificates & secrets section of your Azure AD app registration.
- Add the client ID and client secret from the Azure AD app registration to the associated fields in the Keycloak Identity Providers section.
- Obtain the discovery endpoint from this location:
Your application > Overview > Endpoints > OpenID Connect Metadata Document. - Next, add the discovery endpoint into it's associated text field.
The Discovery endpoint contains the required metadata to use the identity provider. - Once all boxes are filled in, click the Add button.
- Copy the Redirect URI and paste it into your application located here:
Application > Overview > Redirect URIs > Redirect URIs
Note: If an error related to ‘Prompt’ appears, go to the advanced settings tab and change Prompt value from Unspecified to None.
Sign into DMC DB with OpenID Connection
This section covers how to connect DMC with an OpenID to Azure AD.
- On the DMC sign in screen, click the OpenID Connect Login link on the bottom of the dialog.
This will direct you to the Azure AD login page.
- Log in to Azure AD.
This will direct you back to the DMC.
Mappers
Mappers may be used to automate assigning users in Keycloak to roles, groups, or other functions. The example below describes how to configure the mapper to automatically assign groups in Keycloak based on the group in Azure AD.
Keycloak
- Navigate to your Azure AD identity provider in Keycloak and select the Mappers menu.
- Add a custom name.
- Select a sync mode.
Select Force if you want to update the data each time you log in. - Select mapper type Advanced Claim to Group.
- In the Claims section, add groups as theKey.
- In the Claims section, add yourgroup id from Azure AD as theValue.
- In the Group section, select which groups you want to assign to the user when the condition is met.
- Click theSave button.
- Navigate to the Client Scopes section and create a new client scope.
- Add the name groups.
- Click the Save button.
- Change the Assigned Type to Default.
- Navigate to the Azure AD app registration page and select Manifest.
- Change the groupMembershipClaims property value from null to All.
After these steps are complete, the user will be assigned to the provided group the next time they login.
Note: If there are issues when logging out - change the Backchannel logout toggle value in the identity provider advanced settings.
